Revolutionary Cyber Asset Attack Surface Management
Asset Discovery
Asset Discovery
From a handful of devices to hundreds of thousands. CyAmast gives a complete real-time asset inventory that scales without limits
Device Classification
Device Classification
Agnostic to device type, manufacturer, and even encryption, CyAmast passively detects, classifies, and profiles behaviour of new & existing devices
Continuous Monitoring
Continuous Monitoring
CyAmast performs passive real-time monitoring for complete visibility and device behavioral-context to provide better intelligence
Analysis and Action
Analysis and Action
CyAmast gives you the information you need to detect and protect anomalous behaviours before they are fully executed
The Transparency and Insight You Need
The CyAmast platform provides unprecedented visibility and forensic intelligence. By tracking the profiles of individual or groups of devices, the CyAmast reporting functionality can identify abnormalities and rogue activities faster and more accurately than any solution on the market.
CyAmast discovers all active devices on the network. Once discovered, it uses patented machine learning ‘models’ to classify the devices, like CCTV cameras by make and type. Once discovered and classified, a device inventory is kept and automatically updated.
Asset Discovery
Asset Discovery
From a handful of devices to hundreds of thousands. CyAmast gives a complete real-time asset inventory that scales without limits
Device Classification
Device Classification
Agnostic to device type, manufacturer, and even encryption, CyAmast passively detects, classifies, and profiles behaviour of new & existing devices
Continuous Monitoring
Continuous Monitoring
CyAmast performs passive real-time monitoring for complete visibility and device behavioral-context to provide better intelligence
Analysis and Action
Analysis and Action
CyAmast gives you the information you need to detect and protect anomalous behaviours before they are fully executed
CyAmast is changing the way networks are secured. I look forward to seeing how they catalyse the full power of more integrated digital networks by providing a more robust asset management and security solution. It’s very early days in the emerging and complex space of CAASM, but I believe CyAmast and their unique approach to be well-placed to ensure the safety of all networks – from tiny LANs to enterprise – as digital transformation fulfils its global promise, and helps usher in a more empowered world.
How CyAmast Works
For asset management and cyber-health monitoring, it’s time to move past merely matching signatures in packet contents or using MAC address-based device classification. If you only rely on signature-based attack detection, you won’t be able to detect what you don’t know exists, and spoofing can easily thwart methods like MAC address-based inference.
Without the burden and expense of new specialised infrastructure, CyAmast has moved past constrained approaches to asset management. Our solutions automatically and passively create distinctive behavioural profiles of networked assets that are contextualised to your environment. It offers comprehensive and precise real-time asset inventory along with comprehensive anomaly detection in a way that is less resource-intensive, more precise, and more affordable than competing technologies.
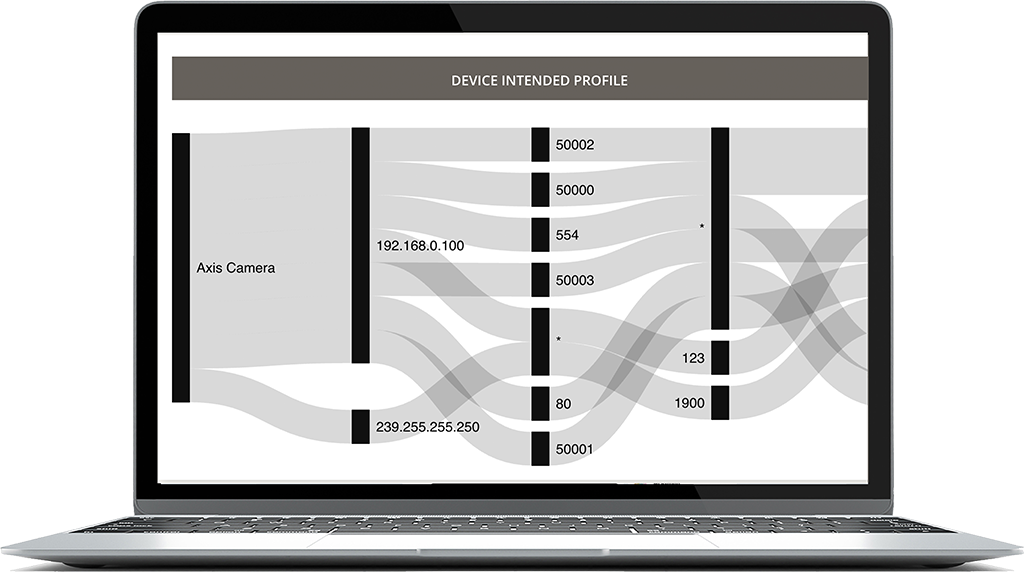
Get the Full Picture
See every device on your network and know that it’s secure and operational.
To see how CyAmast will help you improve the fidelity of your entire network, download our Service Overview document, and then schedule a walk-through with one of our Consultants.


